NEWS
Effect on our products for security update for vulnarebility in DCOM (CVE-2021-26414)
2022.03.15
We inform you of the impact on our products of the security updates (see details) for the vulnerability in DCOM (CVE-2021-26414) as follows.
Effect
In the following configurations using DCOM communication, OPC DA Client may not be able to connect to OPC DA Server after the security update.
- When the OPC DA Client and OPC DA Server are running on different PCs.
-
When OPC DA Client and OPC DA Server are launched by different users. (e.g. running as Service program)
* Communication via OPC UA interface is not affected.
Effect on our products
Communication via OPC DA interface may be affected.
* You can scroll this table sideways.
| Product | Version | Effect |
|---|---|---|
| DeviceXPlorer OPCServer (DxpSERVER) | All version | Affected |
| Sample clients for OPC DA | All version | Affected |
| DA Server | All version | Affected |
| DeviceXPlorer Data Logger (DxpLOGGER) | All version | Affected |
| DeviceGateway | All model, All version | Not affected |
| OPC Spider | All version | Not affected |
| HULFT IoT TAKEBISHI | All version | Not affected |
| FileArk FA Edition | All version | Not affected |
Details of Effect
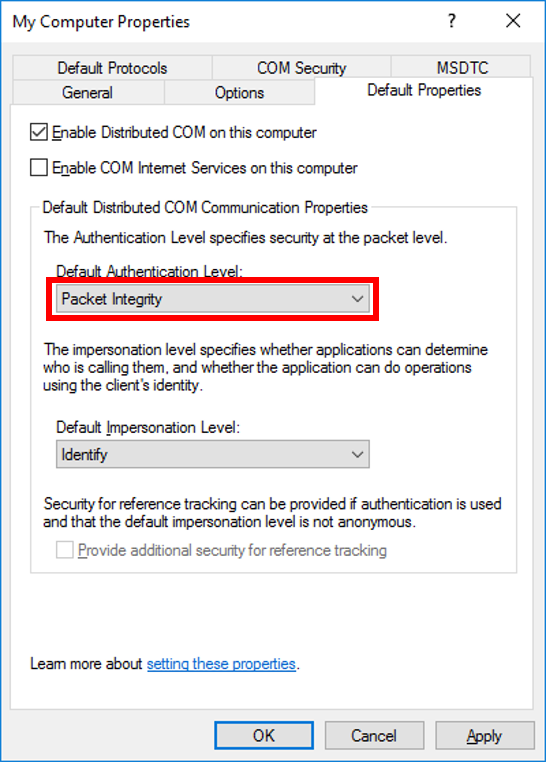
Once the security update to be distributed in June 2022 is applied, the authentication level that can be used on the OPC DA server is set to "RPC_C_AUTHN_LEVEL_PKT_INTEGRITY (packet integrity)" or higher when communicating using DCOM. Therefore, if you specify the authentication level less than "RPC_C_AUTHN_LEVEL_PKT_INTEGRITY (packet integrity)" from OPC DA client, an error may occur and the connection cannot be established.
The authentication level can be specified by CoInitializeSecurity or CoCreateInstanceEx by implementation on the OPC client. When it is not specified by implementing, the authentication level of the DCOM setting specified by the component service of Windows is used.
Countermeasure
OPC DA Client(Implemented in application)
-
If the implementation specifies an authentication level, set the authentication level to "RPC_C_AUTHN_LEVEL_PKT_INTEGRITY (packet integrity)" or higher.
* C++ Sample Client for OPC DA "VcSampleOpc" older than V2.1.0 specifies the authentication level as "RPC_C_AUTHN_LEVEL_NONE (none)" in CoInitializeSecurity, so it is necessary to update to the latest version (V2.1.0 or later) that the authentication level is unspecified. The latest version of C++ Sample Client for OPC DA can be downloaded from the following page.
Both of OPC Server and OPC Client (DCOM settings for Windows)
- Set the authentication level to "Packet Integrity" for My Computer, OPC Enum, and OPC Server settings in the DCOM settings.
For more information on DCOM settings, please refer to DCOM Settings Check List on the following page.

